Crypto greeting cards
Unit 2: Cryptographic Algorithms.
efl cryptocurrency price
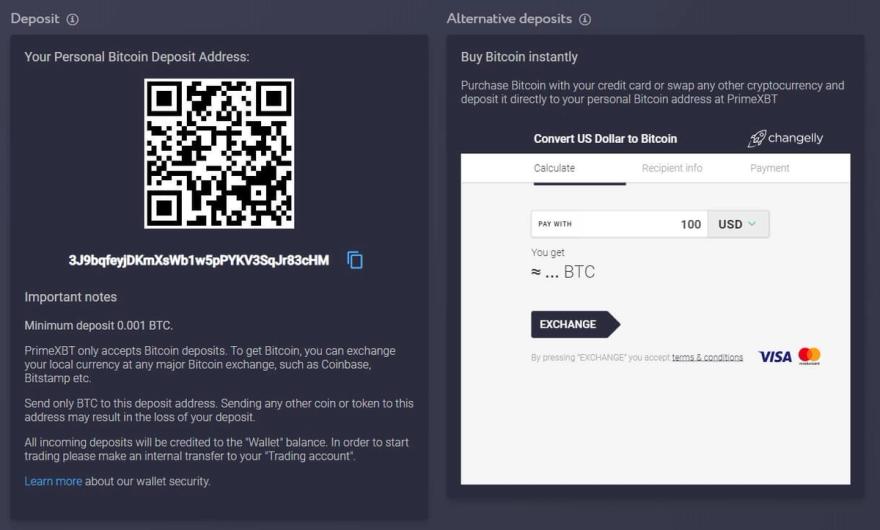
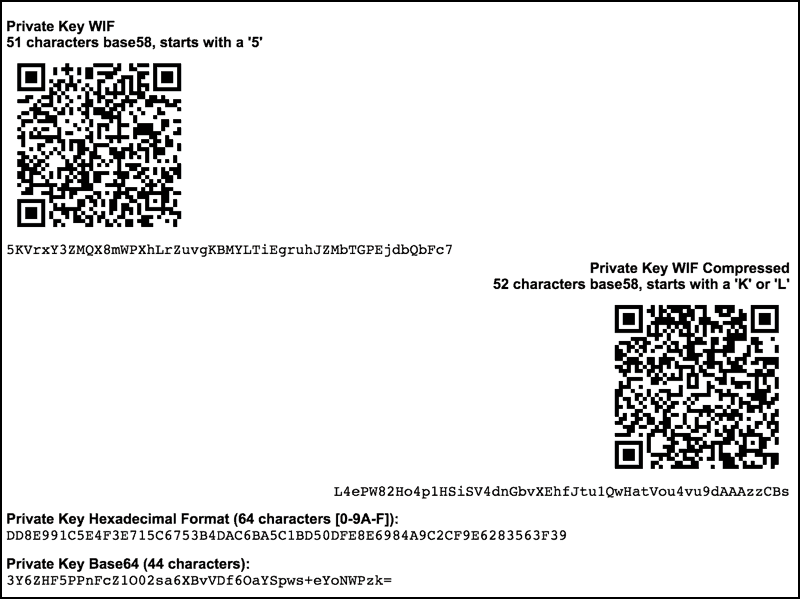
| 128 bit bitcoin private key | Unit 1: Introduction to Bitcoin Technology. To avoid key reuse , webservers should keep track of used keys and never run out of public keys. To make it more convenient to use non-digital backup methods, such as memorization or hand-copying, BIP39 defines a method for creating a bit root seed from a pseudo-sentence mnemonic of common natural-language words which was itself created from to bits of entropy and optionally protected by a password. For details, please see the wallet section in the developer reference or BIP32 for the full HD protocol specification. Private keys are what are used to unlock satoshis from a particular address. |
| 128 bit bitcoin private key | In the subsections below, we will describe common combinations of these parts. Cryptography can also be used to prove knowledge of a secret without revealing that secret digital signature , or prove the authenticity of data digital fingerprint. See the private key encoding section above. Skip to main content. Convert the result from a byte string into a Base58 string using Base58Check encoding. Private keys meant to be used with compressed public keys have 0x01 appended to them before being Base encoded. |
| Crypto for a new world | Shiba inu crypto coin twitter |
| Blockchain developer means | 344 |
| 128 bit bitcoin private key | Crypto wallet app review |
How to buy bitcoins in nz
The mini private key is 30 Base58 characters starting with even if the key is broken into multiple lines for.
The variant known as "Code the string followed by '.
how do i start a crypto currency exchange business
How secure is 256 bit security?Bitcoin has a private key with bits and uses ECC. The elliptic AES) we need a bit elliptic curve � like the one Bitcoin uses. No. What the GP is quoting is "security bits" a measure explicitly designed to mitigate that difference. Bitcoin addresses have bits of security, bits. Before we demonstrate how to generate a public key from a private key, let's look at elliptic curve cryptography in a bit more detail. private key is .
Share: